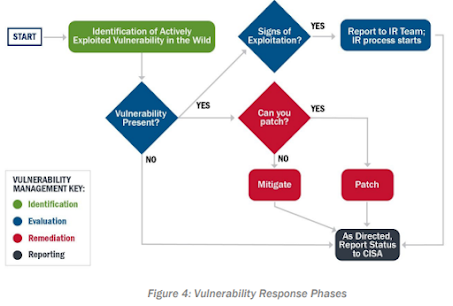
Identification
Proactively identify reports of vulnerabilities that are actively exploited in the wild by monitoring threat feeds and information sources, including but not limited to:
CISA resources; for example:
CISA/US-CERT National Cyber Awareness System (NCAS) products, which include the weekly bulletins containing vulnerability summaries, and
Note: all agencies should subscribe to NCAS products.30
CISA Binding Operational Directive (BOD) 22-01, Managing Unacceptable Risk of Known Vulnerabilities, which is continually updated with vulnerabilities being exploited in the wild.
Note: subscribe to NCAS products for all BOD 22-01 vulnerability updates, which are announced via Current Activities.
External threat or vulnerability feeds, such as NIST’s National Vulnerability Database, 31 that can also show vulnerabilities being exploited in the wild outside FCEB agencies.
Internal SOC monitoring and incident response, which can detect vulnerabilities being exploited at an agency. Capture additional information about the vulnerability to help with the rest of the response process, including the severity of the vulnerability, susceptible software versions, and IOCs or other investigation steps that can be used to determine if it was exploited.
Evaluation
First, determine whether the vulnerability exists in the environment and how critical the underlying software or hardware is, using methodologies such as Stake Holder Specific Vulnerability Categorization (SSVC). 32 Existing patch and asset management tools are critical and can be used to automate the detection process for most vulnerabilities. For actively exploited vulnerabilities, use the “rapid response” processes in these tools (e.g., CDM). In rare cases, such as one-off misconfigurations and zero-days, additional manual scans may need to be performed. Binding Operational Directives (BODs) or Emergency Directives (EDs) issued by CISA may also list specific technical steps to evaluate whether a vulnerability exists. If the vulnerability exists in the environment, address the vulnerability itself—as described in the Remediation section below—and determine whether it has been exploited in the agency's environment.
Use existing best practices to find signs of exploitation, including:
- A sweep for known IOCs associated with exploitation of the vulnerability.
- Investigation of any abnormal activity associated with vulnerable systems or services, including anomalous access attempts and behavior.
- Completion of any detection processes in CISA directives.
- If needed, collaboration with a third-party incident responder.
If the vulnerability was exploited in the environment, immediately begin incident response activities as described in the Incident Response Playbook.
At the end of the Evaluation phase, the goal is to understand the status of each system in the environment as:
- Not Affected -> The system is not vulnerable
- Susceptible -> The system is vulnerable, but no signs of exploitation were found, and remediation has begun
- Compromised -> The system was vulnerable, signs of exploitation were found, and incident response and vulnerability remediation has begun.
Remediation
Remediate all actively exploited vulnerabilities that exist on or within the environment in a timely manner. In most cases, remediation should consist of patching. In other cases, the following mitigations may be appropriate:
- Limiting access
- Isolating vulnerable systems, applications, services, profiles, or other assets
- Making permanent configuration changes
Existing patch management tools and processes can be used to regularly patch all vulnerabilities. Use “rapid response” processes—as described in the Evaluation section above—in those tools for vulnerabilities that are being actively exploited in the wild. In cases where patches do not exist, have not been tested, or cannot be immediately applied promptly, take other courses of action to prevent exploitation, such as:
Disabling services
- Reconfiguring firewalls to block access
- Increasing monitoring to detect exploitation
Once patches are available and can be safely applied, mitigations can be removed, and patches applied. As systems are remediated, keep track of their status for reporting purposes. Each system should be able to be described as one of these categories:
Remediated -> The patch or configuration change has been applied, and the system is no longer vulnerable
Mitigated -> Other compensating controls—such as detection or access restriction—are in place and the risk of the vulnerability is reduced
Susceptible/Compromised -> No action has been taken, and the system is still susceptible or compromised
Reporting and Notification
Sharing information about how vulnerabilities are being exploited by adversaries can help defenders across the federal government understand which vulnerabilities are most critical to patch. CISA, in partnership with other federal agencies, is responsible for the overall security posture of the FCEB. As such, CISA needs to maintain awareness of the status of vulnerability response for actively exploited vulnerabilities. This awareness enables CISA to help other agencies understand the impact of vulnerabilities and to narrow the time between disclosure and vulnerability exploitation. Agencies must report to CISA in accordance with Federal Incident Notification Guidelines, Binding Operational Directives, or as directed by CISA in an Emergency Directive.
Happy Learning !!