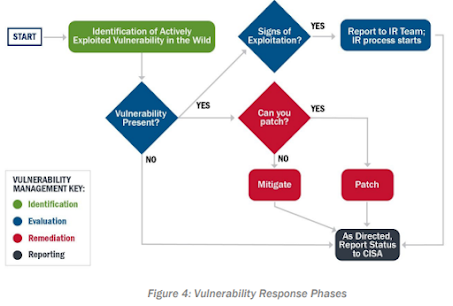
Often due to application dependencies, EOL systems and budget constraints, it is not possible to patch servers. So .. What actions can we take in such situations ? Lookout for answers to the following questions:
1. Is the vulnerability providing information disclosure ?
Your DLP or WAF solution may already be capable of detecting and mitigating against such an exploit.
2. Does the vulnerability call an application to perform an unwanted action ?
It is possible that your Host Based Intrusion Detection System can prevent those binaries from executing.
3. Does the vulnerability require access to a resource or service ?
An ACL that blocks or restricts access might be the perfect solution.
In case of EOL systems, the following compensating controls can be put in place:
1. Network isolation/segmentation
One option to protect EOL devices is to place critical servers on an isolated network to ensure the devices cannot interact with any machines outside of the isolated network or connect to the Internet. With network isolation, EOL devices are protected from threats, but drastically limit access to other critical assets
including internet and cloud functions. While this security model can be used as a compensating control to mitigate threats, this option may pose business disruption and impact end-user productivity since most server host critical applications that need to be connected to corporate servers for employee access.
2. Virtualization
Hosting assets within a virtualized environment can provide a number of security benefits; increased control over critical assets, ease of re-imaging in the event of a compromise, and the ability to limit critical server exposure to an environment. If an asset becomes a target, it can be quickly isolated and re-initialized. But for critical servers running applications that require round-the-clock access, virtualization represents a possibility of increased administration and resources. It can also lead to failed compliance policies by virtue that in-scope data must be controlled or cannot run within a virtual environment.
3. Application control and whitelisting
It is a security model focused on allowing known “good” applications to run rather than blocking known “bad.” By only allowing trusted software to run, application whitelisting will stop exploits and reduce the administration associated with system and application patching and updates. In “default-deny” mode, application whitelisting is a highly effective compensating control to meet regulatory compliance standards and harden out-of-date systems.
Happy Learning !!